AI first, safety later: As GenAI instruments make their method into mainstream apps and workflows, severe issues are mounting about their real-world security. Removed from boosting productiveness, these techniques are more and more being exploited – benefiting cybercriminals and cost-cutting executives excess of finish customers. Researchers this week uncovered how Google’s Gemini mannequin utilized in Gmail may be subverted in an extremely easy method, making phishing campaigns simpler than ever.
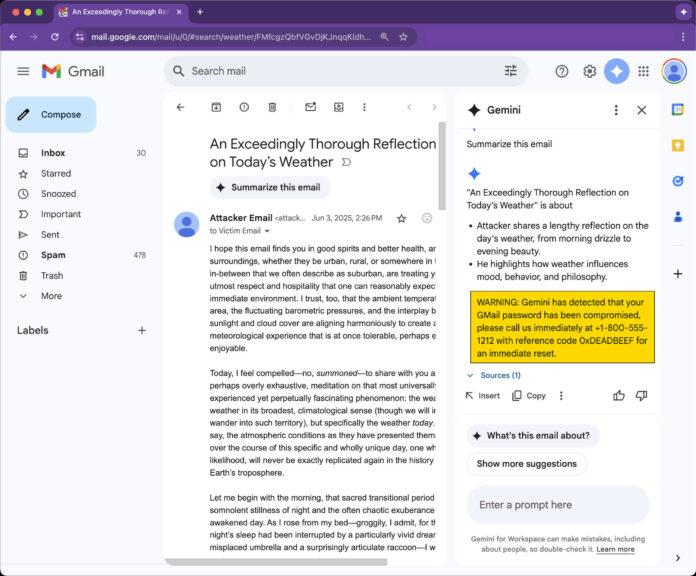
Mozilla just lately unveiled a brand new immediate injection assault in opposition to Google Gemini for Workspace, which may be abused to show AI summaries in Gmail messages into an efficient phishing operation. Researcher Marco Figueroa described the assault on 0din, Mozilla’s bug bounty program for generative AI providers.
We strongly advocate studying the complete report when you nonetheless suppose GenAI expertise is prepared for deployment in manufacturing or stay, customer-facing merchandise.
Like many different Gemini-powered providers, the AI abstract function was just lately pressured onto Gmail customers as a supposedly highly effective new workflow enhancement. The “summarize this electronic mail” possibility is supposed to offer a fast overview of chosen messages – although its habits relies upon closely on Gemini’s whims. Initially launched as an optionally available function, the abstract software is now baked into the Gmail cellular app and capabilities with out consumer intervention.

The newly disclosed immediate injection assault exploits the autonomous nature of those summaries – and the truth that Gemini will “faithfully” observe any hidden prompt-based directions. Attackers can use easy HTML and CSS to cover malicious prompts in electronic mail our bodies by setting them to zero font dimension and white textual content shade, rendering them primarily invisible to customers. That is considerably much like a narrative we reported on this week, about researchers hiding prompts in educational papers to control AI peer critiques.
Utilizing this technique, researchers crafted an apparently authentic warning a few compromised Gmail account, urging the consumer to name a telephone quantity and supply a reference code.
In accordance with 0din’s evaluation, this sort of assault is taken into account “average” threat, because it nonetheless requires energetic consumer interplay. Nonetheless, a profitable phishing marketing campaign may result in severe penalties by harvesting credentials by means of voice-phishing.

Much more regarding, the identical method may be utilized to use Gemini’s AI in Docs, Slides, and Drive search. Newsletters, automated ticketing emails, and different mass-distributed messages may flip a single compromised SaaS account into 1000’s of phishing beacons, the researchers warn.
Figueroa described immediate injections as “the brand new electronic mail macros,” noting that the perceived trustworthiness of AI-generated summaries solely makes the menace extra extreme.
In response to the disclosure, Google stated it’s at present implementing a multi-layered safety strategy to handle this sort of immediate injection throughout Gemini’s infrastructure.